The slow loris assault: The sluggish loris assault is frequently named a DDoS attack, but since the assault targets a certain server (In cases like this, an internet server) and typically will not use intermediate networking equipment, it is typically a traditional DoS attack.
IoT Products: Weaknesses in connected equipment can be exploited by cybercriminals, turning them into zombies. The infamous Mirai botnet was used to launch a series of attacks using unsecured infant monitors.
Hiện nay, ngành công nghiệp sport đã chuyển dịch cơ cấu sang loại hình online, từ sự phát triển thể loại MMO cho đến các dịch vụ trung gian như Steam hay Garena, thậm chí các recreation offline cũng có chế độ Multiplayer để đảm bảo kết nối nhiều người chơi với nhau.
Carry out mock exercises for DDoS assaults. This will include planned or shock workout routines to correctly educate IT execs, employees and management on reaction things to do.
A CharGEN attack includes attacking equipment that utilize the Character Generator Protocol for screening and debugging.6 Other common attacks contain zero-working day assaults, which exploit coding faults, and packet flood assaults.
In recent times, numerous sectors have claimed increasing costs of sector-distinct DDoS assaults starting from manufacturing ddos web and retail to monetary institutions and in some cases governments. The May possibly, 2021 assault on the Belgium federal government afflicted a lot more than 200 businesses.
A DDoS assault normally requires a botnet—a community of Net-connected products which were contaminated with malware that permits hackers to manage the equipment remotely.
Attackers spoofed GitHub’s IP tackle, attaining access to Memcache scenarios to boost the traffic volumes aimed at the platform. The Corporation speedily alerted aid, and targeted visitors was routed by way of scrubbing centers to limit the damage. GitHub was back again up and managing inside of 10 minutes.
Amplification: This really is an extension of reflection, where the reaction packets sent on the victim by the 3rd-party units are much larger in sizing compared to the attackers’ packets that activated the responses.
Equipment referred to as bootersand stressersare out there on the dim web that essentially offer DDoS-as-a-assistance to interested buyers, offering entry to readymade botnets at the press of a button, for just a price.
La protección DDoS garantiza que los sitios World-wide-web y las aplicaciones permanezcan en línea y seguros, velando por que la experiencia del usuario sea positiva.
The week of April 27, a barrage of cyberattacks broke out, The majority of them of the DDoS assortment. Folks made use of ping floods and botnets to spam and take down a lot of economical institutions, authorities departments and media retailers. This assault continues to be considered to be One of the more innovative to this point and is particularly a reliable illustration of a point out-run DDoS assault.
March 2024: A group of Russia-aligned hacktivists disrupted several French federal government expert services which has a series of DDoS assaults.
Although organizations in almost any sector are susceptible, these sectors are subject to DDoS assaults most often:
 Michael C. Maronna Then & Now!
Michael C. Maronna Then & Now! Freddie Prinze Jr. Then & Now!
Freddie Prinze Jr. Then & Now!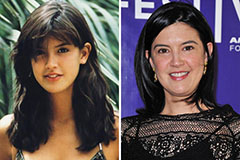 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Jeri Ryan Then & Now!
Jeri Ryan Then & Now! Terry Farrell Then & Now!
Terry Farrell Then & Now!